Maintaining Unix Attributes in AD using ADUC: Difference between revisions
No edit summary |
|||
| Line 54: | Line 54: | ||
= Curses ADUC = |
= Curses ADUC = |
||
You can alternatively use the curses ADUC module to maintain Unix Attributes in AD. You can download an [https:// |
You can alternatively use the curses ADUC module to maintain Unix Attributes in AD. You can download an [https://appimage.github.io/admin-tools/ AppImage here]. |
||
= Setting attributes on an user account = |
= Setting attributes on an user account = |
||
Latest revision as of 19:55, 6 August 2019
Introduction
In the following we describe how to set/edit the RFC2307 attributes used by idmap_ad. This requires to have NIS extensions installed in your AD. To administer the UNIX attributes via the Windows GUI you should install the Remote Server Administration Tools (RSAT), if not already installed and enable the advanced view ("View" / "Advanced features"). Modifications on user and group objects will be done by the Domain Administrator, if you haven't set any delegations.
| ADUC, running on Windows 10 and Windows Server 2016, no longer displays the "Unix Attributes" tab in user or group properties. For details, see Missing Unix Attributes tab in ADUC on Windows 10 and Windows Server 2016. |
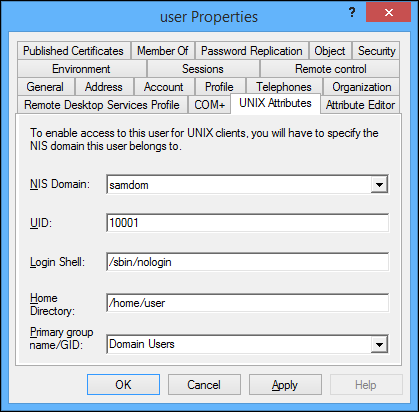
Setting attributes on an user account
- Open ADUC.
- Right-click to a user account and choose properties.
- Navigate to the "UNIX Attributes" tab.
- Note: If you don't see this tab, you haven't installed the RSAT function "Server for NIS Tools".
- The other fields are not enabled until the "NIS Domain" is chosen. Fill the values as required.
- Hint: You can only choose a primary group that has had Unix attributes defined!
- Click "OK" to save your changes.
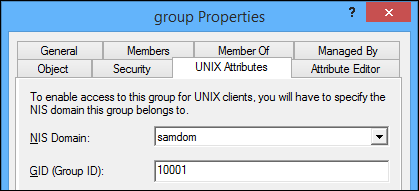
Setting attributes on a group
- Open ADUC.
- Right-click to a group and choose properties.
- Navigate to the "UNIX Attributes" tab.
- Note: If the tab isn't visible, you haven't installed the RSAT function "Server for NIS Tools".
- The other fields are not enabled until the "NIS Domain" is chosen, fill the values as required.
- Hint: It's not required to add users to the group in this tab! Winbind retrieves the account membership from the Windows groups (see "Member Of"-tab).
- Click "OK" to save your changes.
Curses ADUC
You can alternatively use the curses ADUC module to maintain Unix Attributes in AD. You can download an AppImage here.
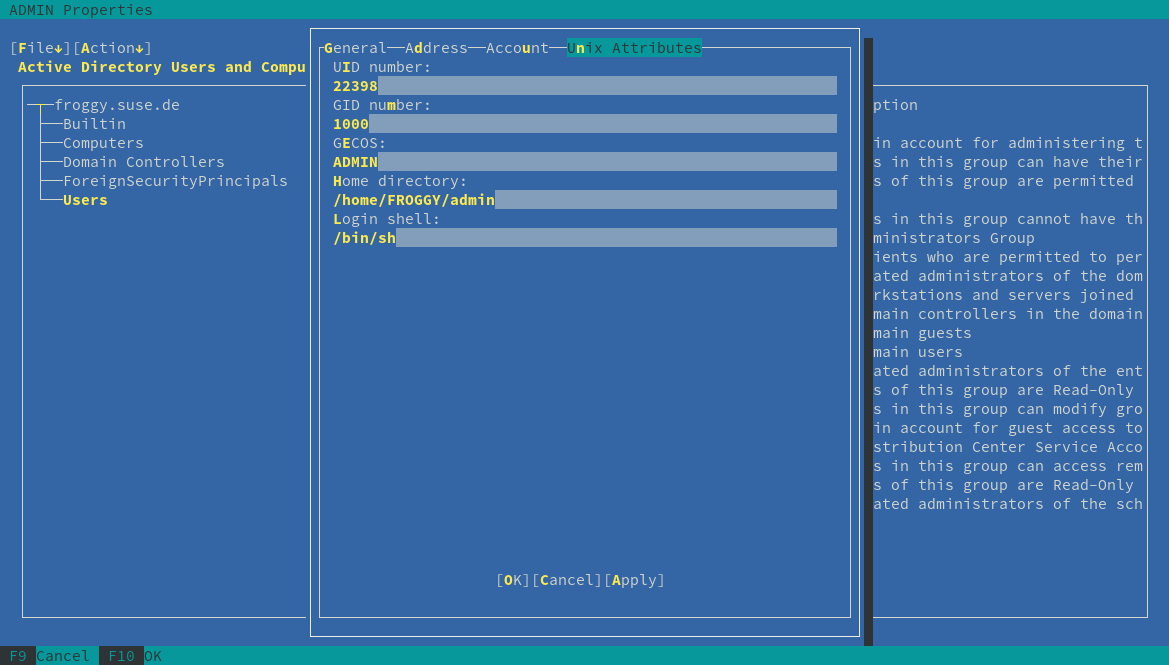
Setting attributes on an user account
- Run the admin-tools AppImage, then choose Active Directory Users and Computers.
- Right-click on a user account and choose properties.
- Navigate to the "UNIX Attributes" tab.
- Click "OK" to save your changes.
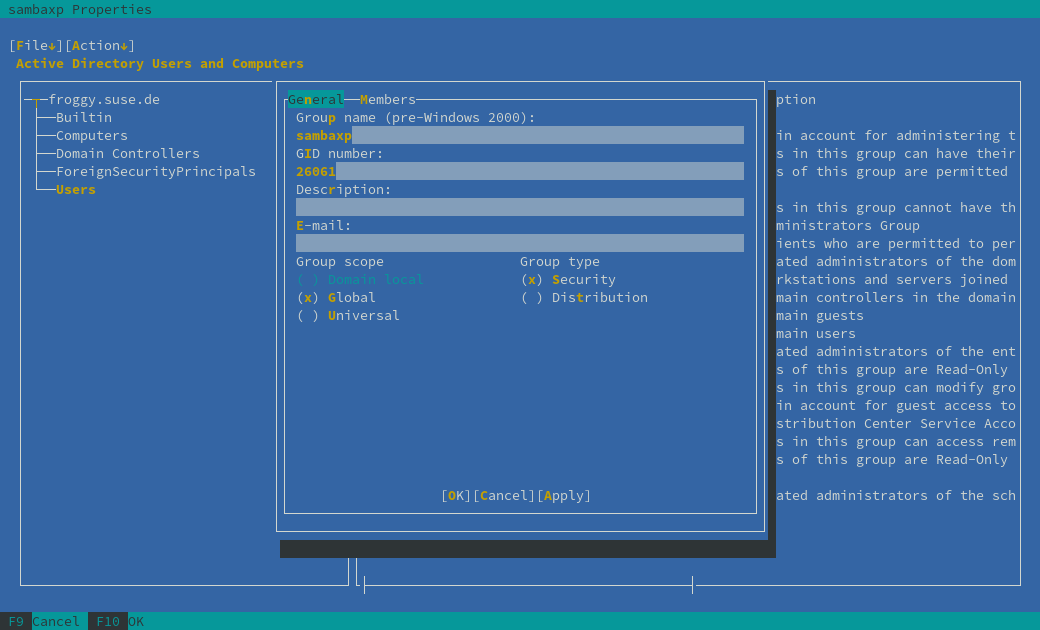
Setting attributes on a group
- Run the admin-tools AppImage, then choose Active Directory Users and Computers.
- Right-click on a group and choose properties.
- Click "OK" to save your changes.
Setting attributes on a computer account
You need to set the uidNumber attribute to access samba shares on a domain with the Windows machine network account.
- Open ADUC.
- Right-click to a computer account and choose properties.
- Navigate to the "Attribute Editor" tab.
- Note: If you don't see this tab, you haven't installed the RSAT function "Server for NIS Tools".
- Scroll down to the "uidNumber" attribute, select it, click edit, enter a value, click "OK"
- Note: Ensure that you enter a unique value.
- Click "OK" to save your changes.
Defining the next UID/GID number to use
Every time a UID/GID number is assigned using Active Directory Users and Computers (ADUC), the next UID/GID number is stored inside the Active Directory. By default, ADUC starts assigning UID and GID numbers at 10000.
If you setup a new Samba AD and want to use a different start value, you will need to add the counting attributes before using ADUC for the first time:
# ldbedit -H /usr/local/samba/private/sam.ldb -b \ CN=samdom,CN=ypservers,CN=ypServ30,CN=RpcServices,CN=System,DC=samdom,DC=example,DC=com
msSFU30MaxUidNumber: 10000 msSFU30MaxGidNumber: 10000