Joining a Windows Server 2012 / 2012 R2 DC to a Samba AD: Difference between revisions
Mmuehlfeld (talk | contribs) m (Fix link) |
Mmuehlfeld (talk | contribs) (Rewrote Windows Server 2012/2012 R2 DC to a Samba AD) |
||
| Line 1: | Line 1: | ||
= Introduction = |
= Introduction = |
||
Samba 4.5 introduces support for the directory schemas 56 (Windows Server 2012) and 67 (Windows Server 2012 R2). However, you cannot join the first Windows Server 2012 or 2012 R2 domain controller (DC) directly to a Samba Active Directory (AD), because it uses the Windows management instrumentation (WMI) protocol for several tasks during the process. To work around, you require a Windows Server 2008 or 2008 R2 DC in the domain to join the first 2012 or 2012 R2 DC. After the first DC with this Windows Server version is joined and the directory schema updated, you can this one as replication partner when you join other Windows 2012 or 2012 R2 DCs. |
|||
== WARNING == |
|||
'''Windows Server 2012 and 2012 R2 as a DC, and the directory schemas 56 and 67 are experimental.''' If you encounter a bug, please report at https://bugzilla.samba.org. |
|||
'''Samba based AD currently doesn't support joining a Microsoft Windows 2012/2012R2 Server <u>as a Domain Controller</u> to a Samba Active Directory! Joining as a Member Server works. Follow the [[Joining_a_Windows_Client_or_Server_to_a_Domain|respective documentation]].''' |
|||
'''This documentation describes the necessary steps and workarounds required for this task. Because of the missing 2012/2012R2 AD schema support in Samba, the join will break your installation!''' |
|||
'''This documentation is for research and debugging only, until all problems and limitations are fixed!''' |
|||
'''Only use this documentation <u>in labs for testing purposes and not in production</u>, because this process will break replication and the AD database!!!''' |
|||
= Warning = |
|||
'''Joining a Windows Server 2012 or 2012 R2 DC to a Samba AD breaks the AD replication! Do not use this documentation until the problem is fixed!''' |
|||
== KNOWN LIMITATIONS == |
|||
For more details, see [https://bugzilla.samba.org/show_bug.cgi?id=12204 Bug #12204]. |
|||
* Samba is shipped with AD schema version 47 (Windows Server 2008 R2). To join a newer version as DC, this schema has to be updated to 56 (Windows Server 2012) or 69 (Windows Server 2012 R2). The Samba AD database backend currently doesn't support all the changes introduced by the new schemas. This would lead to broken replication between Samba and Windows DCs for the affected directory partitions, this cannot be fixed at the moment! '''In simple words: A broken replication makes the AD inconsistent and will destroy your AD!''' |
|||
* At least one [[Joining_a_Windows_Server_2008_/_2008_R2_DC_to_a_Samba_AD|Windows Server 2008 / 2008R2 DC]] is required in the domain, because 2012 replicates the AD content via WMI (Windows Management Instrumentation) from the Schema Master, this isn't implemented yet in Samba. This Windows DC must also have an accessible SysVol share, as 2012 syncronizes its content via DFS-R protocol („SysVol Replication“), which also isn't implemented in Samba yet. |
|||
= Requirements and Known Limitations = |
|||
== Server information == |
|||
* All Samba DCs must run 4.5.0 or later. For information about updating, see [[Updating_Samba|Updating Samba]]. |
|||
This documentation uses the following configuration/settings: |
|||
* Windows Server 2012 and 2012 R2 requires the Windows management instrumentation (WMI) protocol during the join, and for the forest and domain preparation. Samba currently does not support this protocol. Thus you must have an existing Windows domain controller (DC) with WMI support in your domain. For example, you can a Windows Server 2008 or 2008 R2 DC as replication partner during the join. For further information, see [[Joining_a_Windows_Server_2008_/_2008_R2_DC_to_a_Samba_AD|Joining a Windows Server 2008 / 2008 R2 DC to a Samba AD]]. |
|||
'''Existing Samba DCs in the domain:''' |
|||
Domain Controllers: DC1 (10.99.0.1), DC2 (10.99.0.2) |
|||
DCs act also as a DNS server: yes |
|||
'''Existing Windows 2008R2 DC in the domain:''' |
|||
Domain Controller: DC3 (10.99.0.3) |
|||
'''Domain information:''' |
|||
DNS Domain Name: samdom.example.com |
|||
NT4 Domain Name (NETBIOS): SAMDOM |
|||
DNS Servers: 10.99.0.1, 10.99.0.2 |
|||
Domain Administrator: Administrator |
|||
Domain Administrator Password: passw0rd |
|||
'''DC additionally joined to the domain:''' |
|||
Hostname: DC4 |
|||
IP Address: 10.99.0.4 |
|||
Operating System: Microsoft Windows Server 2012 R2 |
|||
| Line 48: | Line 28: | ||
= Network Configuration = |
|||
= Installation / Preparation = |
|||
* Click the "Start" button, search for "View network connections", and open the search entry. |
|||
== General == |
|||
* Right-click to your network adapter and select "Properties". |
|||
* Install Windows Server 2012 / 2012 R2. |
|||
* Configure the IP settings: |
|||
:* Assign a static IP address, enter the subnet mask, and default gateway. |
|||
:* Enter the IP of a DNS server that is able to resolve the Active Directory (AD) DNS zone. |
|||
* Click "OK" to save the settings. |
|||
== Date And Time Settings == |
|||
Active Directory uses Kerberos for authentication, which relies on a fairly consistent time across the network. This makes it necessary, that, before you can join the client to the Domain, the time on the client does not differ more than [http://technet.microsoft.com/en-us/library/cc779260%28v=ws.10%29.aspx 5 minutes] (default setting in an AD) to your Domain Controller. |
|||
* Search for „Network and Sharing Center“ |
|||
:[[Image:Join_Win2012R2_Search_Date_and_time_settings.png]] |
|||
= Date and Time Settings = |
|||
* Check your date, time and time zone settings. |
|||
Active Directory uses Kerberos for authentication. Kerberos requires that the domain member and the domain controllers (DC) are having a synchronous time. If the difference exceeds [http://technet.microsoft.com/en-us/library/cc779260%28v=ws.10%29.aspx 5 minutes] (default), the client is not able to access domain resources for security reasons. |
|||
Before you join the domain, check the time configuration: |
|||
* Open the "Control Panel". |
|||
== Configure Network == |
|||
* Navigrate to "Clock, Language and Region". |
|||
* Search for „Network and Sharing Center“ |
|||
* Click "Date and Time". |
|||
:[[Image:Join_Win2012R2_Search_Network_Sharing_Center.png]] |
|||
* Verify the date, time, and time zone settings. Adjust the settings, if necessary. |
|||
* Click „Change adapter settings“ |
|||
* Click "OK" to save the changes. |
|||
* Right-click to your network connection and choose „properties“ |
|||
* Configure the IP properties. Make sure, that you use a DNS server, that is authoritative for your AD DNS domain! |
|||
:[[Image:Join_Win2012R2_IP_Configuration.png]] |
|||
= FSMO Roles = |
|||
When you join the first Windows Server 2012 or 2012 R2 host as a domain controller (DC) to an Active Directory (AD) forest, the directory schema and the domain are updated. This update must run on a Windows 2008 or 2008 R2 domain controller (DC). For updating the forest and directory schema, transfer the following two flexible single master operation (FSMO) roles to the Windows DC that is already a domain member: |
|||
* Schema Master |
|||
== FSMO Roles == |
|||
* Infrastructure Master |
|||
To transfer the two FSMO roles to a Windows Server 2008 or 2008 R2 DC, see [[Transfering_and_Seizing_FSMO_Roles#Windows_FSMO_Role_Management|Transfering and Seizing FSMO_Roles]]. |
|||
As mentioned in the [[#KNOWN_LIMITATIONS|KNOWN LIMITATIONS]] section, joining a Windows Server 2012 / 2012 R2 requires an AD schema update. Because the Samba AD database backend doesn't support these changes yet, it's neccessary that the involed Schema Master (forest) and the Infrastructure Master (domain) FSMO role are hold by an already joined Windows 2008 / 2008 R2 DC. This allows the update to proceed, but will irrevocable break the replication with all Samba DCs! <u>This is the main reason, why this documentation is not for usage in production environments!</u> |
|||
If you successfully updated the schema during the first Windows Server 2012 or 2012 R2 join, you can later transfer the roles to a Samba DC again. |
|||
'''Note that this is a necesary requirement and the forest or domain preparation fails if a Samba DC holds one or both roles during the first Windows Server 2012 or 2012 R2 DC is joined!''' |
|||
=== Schema Master FSMO Role === |
|||
This step is a workaround, because since Server 2012, the DC promotion process uses WMI (Windows Management Instrumentation), to retrieve data from the Schema Master. |
|||
See the documentation about [[Transfering_and_Seizing_FSMO_Roles#Windows_FSMO_Role_Management|Windows GUI tools, to transfer the Schema Master role]]. |
|||
=== Infrastructure Master FSMO Role === |
|||
= Installing the Active Directory Domain Services = |
|||
This workaround is required, because after updating the schema on the Schema Master of the forest, the Infrastructure Master is involved when preparing the domain for the new schema. Because after the schema update - what will break the replication with Samba DCs - it wouldn't be possible to do the preparation against a Samba DC any more. |
|||
* Start the "Server Manager". |
|||
See the documentation about [[Flexible_Single-Master_Operations_(FSMO)_roles#FSMO_role_management_using_the_Windows_GUI|Windows GUI tools, to transfer the Infrastructure Master role]]. |
|||
* Click "Add roles and features". |
|||
* Select "Role-based or feature-based installation" and click "Next". |
|||
* Click "Select a server from the server pool" and select the local Windows Server from the list. Click "Next". |
|||
* Select "Active Directory Domain Services", including all dependencies. Click "Next". |
|||
* You do not need to select any additional features. Click "Next". |
|||
The folling steps have to executed on the 2012 / 2012 R2 host, that should be joined as a DC later. Do this locally on this host or use RSAT on Windows 8 / 8.1 to execute the commands remotely. |
|||
* |
* Start the installation. |
||
* Click |
* Click "Close". |
||
:[[Image:Join_Win2012R2_Server_Manager.png]] |
|||
* Choose „Role-based or feature-based installation“. Click „Next“. |
|||
* „Select a server from the server pool“ and choose the Windows Server out of the list, where to install the AD DC features. Click „Next“. |
|||
* Choose „Active Directory Domain Services“ from the list, including all dependencies. Click „Next“. |
|||
= Joining the Windows Server to the Domain = |
|||
* Add additional features, if wanted. Click „Next“. |
|||
* Log in to your Windows Server 2012 or 2012 installation using the local administrator account. |
|||
* Start the installation |
|||
* Start the "Server Manager". |
|||
* Click „Close“, after the installation is finished. |
|||
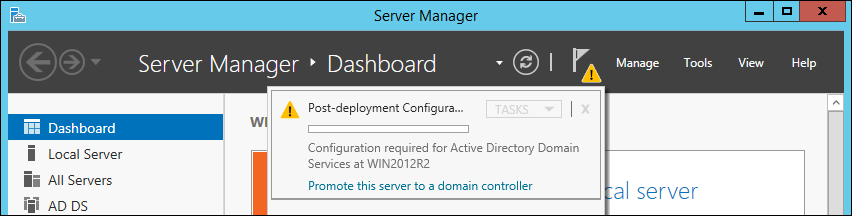
* Click the notifier icon on the top navigation bar and click "Promote this server to a domain controller". |
|||
:[[Image:Join_Win2012R2_Server_Manager_Post_Deployment.png]] |
|||
* Select "Add a domain controller to an existing domain", enter the Samba Active Directory (AD) domain name and credentials that are enabled to join a domain controller (DC) to the domain, like the domain administrator account. Click "Next". |
|||
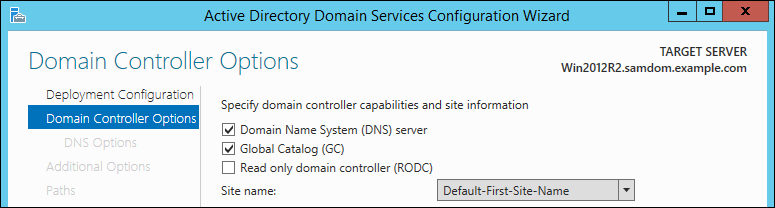
* Select the options to enable on the new DC and enter the directory services restore mode (DSRM) password. It is required to boot the Windows DC in safe-mode to restore or repair the AD in case of problems. Click "Next". |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page2.png]] |
|||
= Updating the schema = |
|||
* If you enabled the "DNS server" option in the previous step, you may see a note, that a delegation for this DNS server cannot be created. Click "Next". |
|||
'''WARNING: This steps will break your Samba AD! Only do this in a lab environment for testing purposes!''' |
|||
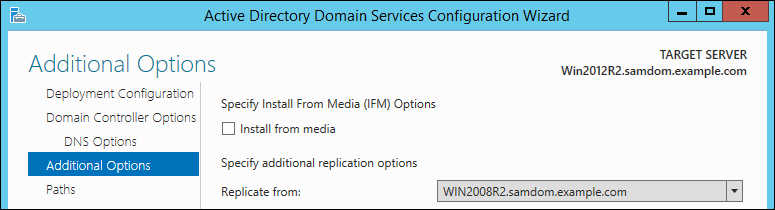
* Samba currently does not support schema replication using the Windows management instrumentation (WMI) protocol. For this reason, select an existing Windows Domain Controller in the domain as replication source and click "Next". |
|||
The following steps have to be executed on the Windows 2008/2008 R2 DC, that owns the Schema Master and Infrastructure Master role: |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page3.png]] |
|||
* Log into the existing 2008 / 2008 R2 DC, using an account, that is member of the universal groups „Schema Admins“ and „Enterprise Admins“. |
|||
* Set the folders for the AD database, log files and the Sysvol folder. Click "Next". |
|||
* Click "Next" to confirm the operations, Windows is going to perform. |
|||
* Verify your settings and click "Next" to start the prerequisite check. |
|||
* Windows runs some prerequisites checks. If any errors are displayed, fix them before you continue. Click "Install". |
|||
* The DC promotions begins. |
|||
: If this is the first Windows Server 2012 or 2012 R2 DC in your AD forest: |
|||
: '''Warning: This step breaks the AD directory replication!''' For more details, see [[#Warning|Warning]]. |
|||
: The installation wizzard is only able to run the AD forest preparation. The domain preparation step fails. To work around: |
|||
:* Log in using the domain administrator account to your existing Windows Server 2008 or 2008 R2 installation that owns the "Schema Master" and the "Infrastructure Master" flexible single master operation (FSMO) role. |
|||
* Insert the Windows 2012 |
:* Insert the Windows Server 2012 or Windows 2012 R2 installation DVD. |
||
* Open a |
:* Open a command line and change to the "support\adprep" folder on the installation DVD. For example, if you DVD drive is "D": |
||
> D: |
> D: |
||
> cd support |
> cd support\adprep\ |
||
:* Start the domain preparation: |
|||
:[[Image:Join_Win2012R2_Adprep_DVD.png]] |
|||
> adprep /domainprep |
|||
* Start the forest preparation (schema update on forest level) by executing |
|||
:* You see the following message if the preparation succeeds: |
|||
> adprep.exe /forestprep |
|||
Adprep successfully updated the domain-wide information. |
|||
:[[Image:Join_Win2012R2_Adprep_Forestprep.png]] |
|||
:A successful run should end with the message |
|||
:* Restart the [[#Joining_the_Windows_Server_to_the_Domain|Joining the Windows Server to the Domain]] process. |
|||
Adprep successfully updated the forest-wide information. |
|||
* If the wizzard completes successfully, the Windows server is restarted automatically. |
|||
:'''After this step the replication between Windows and Samba DCs is broken!'''. On Samba DCs, this can be seen for all inbound connections from Windows DCs. Example: |
|||
* Verify that all DC related DNS records have been created during the promotion. See [[Verifying and Creating a DC DNS Record|Verifying and Creating a DC DNS Record]]. |
|||
# samba-tool drs showrepl |
|||
: '''Do not continue without checking the DNS records. They must exist for a working directory replication!''' |
|||
..... |
|||
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\DC3 via RPC |
|||
DSA object GUID: 691da691-4996-49a0-b5d8-347111d4aa5d |
|||
Last attempt @ Sat Dec 20 18:20:14 2014 CET <u>failed, result 1359 (WERR_INTERNAL_ERROR)</u> |
|||
28 consecutive failure(s). |
|||
Last success @ Sat Dec 20 18:15:14 2014 CET |
|||
* Continue executing the domain preparation. There should be no output and only a success message: |
|||
:[[Image:Join_Win2012R2_Adprep_Domainprep.png]] |
|||
:This step will fail, if the Infrastructure Master role wasn't transfered to a Windows host, <u>before</u> updating the schema. In the domain preparation, the Infrastructure Master is involeved. And because of the broken replication after preparing the forest, the changes won't reached the Samba DCs. That's why the domainprep step can't be executed against a Samba DC any more! |
|||
= Verifying the Directory Replication = |
|||
A few minutes after the domain controller (DC) started, the connections with all other DCs are automatically established and the replication begins. |
|||
To verify the directory replication, run on a Samba DC: |
|||
# samba-tool drs showrepl |
|||
= Promote Windows Server 2012 / 2012 R2 to a Domain Controller = |
|||
Default-First-Site-Name\SAMBADC |
|||
DSA Options: 0x00000001 |
|||
DSA object GUID: 4a6bd92a-6612-4b15-aa8c-9ec371e8994f |
|||
DSA invocationId: 96bc0d6f-9cea-4011-b9a1-0e9971009b20 |
|||
==== INBOUND NEIGHBORS ==== |
|||
DC=DomainDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ NTTIME(0) was successful |
|||
0 consecutive failure(s). |
|||
Last success @ NTTIME(0) |
|||
DC=DomainDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ NTTIME(0) was successful |
|||
0 consecutive failure(s). |
|||
Last success @ NTTIME(0) |
|||
DC=ForestDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ NTTIME(0) was successful |
|||
0 consecutive failure(s). |
|||
Last success @ NTTIME(0) |
|||
DC=ForestDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ NTTIME(0) was successful |
|||
0 consecutive failure(s). |
|||
Last success @ NTTIME(0) |
|||
DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:35:09 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:09 2014 CET |
|||
DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:35:09 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:09 2014 CET |
|||
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:35:10 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:10 2014 CET |
|||
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:35:10 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:10 2014 CET |
|||
CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:35:11 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:11 2014 CET |
|||
CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:35:11 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:11 2014 CET |
|||
==== OUTBOUND NEIGHBORS ==== |
|||
DC=DomainDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:17 2014 CET |
|||
DC=DomainDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:17 2014 CET |
|||
DC=ForestDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:17 2014 CET |
|||
DC=ForestDnsZones,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:35:17 2014 CET |
|||
DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:34:26 2014 CET |
|||
DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:34:26 2014 CET |
|||
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:34:26 2014 CET |
|||
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:34:26 2014 CET |
|||
CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2008R2DC via RPC |
|||
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9 |
|||
Last attempt @ Sat Dec 20 10:34:21 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:34:21 2014 CET |
|||
CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Default-First-Site-Name\Win2012R2DC via RPC |
|||
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Last attempt @ Sat Dec 20 10:34:21 2014 CET was successful |
|||
0 consecutive failure(s). |
|||
Last success @ Sat Dec 20 10:34:21 2014 CET |
|||
==== KCC CONNECTION OBJECTS ==== |
|||
Connection -- |
|||
Connection name: f55bce90-d458-400a-a4ca-801c3e64bef3 |
|||
Enabled : TRUE |
|||
Server DNS name : Win2008R2DC.samdom.example.com |
|||
Server DN name : CN=NTDS Settings,CN=Win2008R2DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
TransportType: RPC |
|||
options: 0x00000001 |
|||
Warning: No NC replicated for Connection! |
|||
Connection -- |
|||
Connection name: fb03f58b-1654-4a02-8e11-f0ea120b60cc |
|||
Enabled : TRUE |
|||
Server DNS name : Win2012R2DC.samdom.example.com |
|||
Server DN name : CN=NTDS Settings,CN=Win2012R2DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
TransportType: RPC |
|||
options: 0x00000001 |
|||
Warning: No NC replicated for Connection! |
|||
It can take several minutes until all connections are established. If the connections on existing Samba DCs to the Windows DC are not established within 15 minutes, start the replication manually. For details, see [[Samba-tool_drs_replicate|samba-tool drs replicate]]. |
|||
The following steps are executed on the 2012 / 2012 R2 host, that should be joined as a DC to the domain: |
|||
If you are seeing the warning "No NC replicated for Connection!", see [[FAQ#Message:_Warning:_No_NC_replicated_for_Connection.21|FAQ: Warning: No NC replicated for Connection!]]. |
|||
* In the Server Manager, click the notify icon, that indicates a outstanding „Post-deployment Configuration“ task and choose „Promote this server to a domain controller“. |
|||
:[[Image:Join_Win2012R2_Server_Manager_Post_Deployment.png]] |
|||
* Select „Add a domain controller to an existing domain“, enter the domain name and credentials, that are allowed to join a DC to the domain. Afterwards click „Next“ |
|||
== Testing the Directory Replication == |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page1.png]] |
|||
To test that the directory replication works correctly, add for example a user on an existing DC and verify that it shows up automatically on the new promoted Windows DC. |
|||
* Set the Domain Controller capabilities, site information and the Directory Service Restore Mode password. The DSRM passwort is used to boot the Windows DC in a safe-mode, to restore or repair the AD. We assume here, to install the new DC with „DNS server“ and „Global catalog“. To continue, choose „Next“. |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page2.png]] |
|||
* If you receive a message, that a delegation for this DNS server cannot be created, ignore it and continue with „Next“. |
|||
* Choose a Windows (!) Domain Controller to replicate from. This is necessary, because the schema is replicated via WMI and the SysVol content via FRS. Both is not supported by Samba yet. Click „Next“ to continue. |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page3.png]] |
|||
= The Sysvol Share = |
|||
* Adapt the folder locations, if desired. Click „Next“. |
|||
During the join, Windows tries to replicate the Sysvol directory content from an existing domain controller (DC). Samba currently does not support the DFS-R protocol. For this reason, the new DC may not show a "Sysvol" share. To enable the share: |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page4.png]] |
|||
* Save the following content to a plain text file named "Win-Create-Sysvol-Share.reg" using a text editor like "Notepad" or "Editor" (not Word/Wordpad/OpenOffice/LibreOffice/etc.): |
|||
Windows Registry Editor Version 5.00 |
|||
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters] |
|||
"SysvolReady"=dword:00000001 |
|||
* Log in using an account that is member of the local "Administrators" group. |
|||
* Review your settings. Click „Next“. |
|||
* Double-click the file to import it to the Windows registry. |
|||
* Windows executes some prerequisites checks. While warnings are Ok, any errors have to be solved, before you can continue. Click „Install“, to begin the DC promotion. |
|||
* Reboot to take the changes effect. |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page5.png]] |
|||
:Notice: During the join of the first 2012 / 2012 R2 DC in a forest, the schema is updated, if it wasn't done [[#Updating_the_schema|before]]. The automatic update during the join would fail in a Samba / Windows mixed envionment. That's why we [[#Updating_the_schema|had updated the schema before]]. |
|||
* The DC promotions begins. If the wizzard finishes its work successful, a message is shown for a short moment, before the new DC automatically reboots. |
|||
== Sysvol replication == |
|||
:[[Image:Join_Win2012R2_DS_Wizzard_Page6.png]] |
|||
Samba currently does not support the DFS-R protocol required for Sysvol replication. Please manually synchronise the content between DC or use a workaround like [[Robocopy_based_SysVol_replication_workaround|Robocopy-based Sysvol Replication]]. |
|||
* After the reboot, you can log into the new joined Windows Server 2012 / 2012 R2 Domain Controller. |
|||
Revision as of 17:57, 6 September 2016
Introduction
Samba 4.5 introduces support for the directory schemas 56 (Windows Server 2012) and 67 (Windows Server 2012 R2). However, you cannot join the first Windows Server 2012 or 2012 R2 domain controller (DC) directly to a Samba Active Directory (AD), because it uses the Windows management instrumentation (WMI) protocol for several tasks during the process. To work around, you require a Windows Server 2008 or 2008 R2 DC in the domain to join the first 2012 or 2012 R2 DC. After the first DC with this Windows Server version is joined and the directory schema updated, you can this one as replication partner when you join other Windows 2012 or 2012 R2 DCs.
Windows Server 2012 and 2012 R2 as a DC, and the directory schemas 56 and 67 are experimental. If you encounter a bug, please report at https://bugzilla.samba.org.
Warning
Joining a Windows Server 2012 or 2012 R2 DC to a Samba AD breaks the AD replication! Do not use this documentation until the problem is fixed! For more details, see Bug #12204.
Requirements and Known Limitations
- All Samba DCs must run 4.5.0 or later. For information about updating, see Updating Samba.
- Windows Server 2012 and 2012 R2 requires the Windows management instrumentation (WMI) protocol during the join, and for the forest and domain preparation. Samba currently does not support this protocol. Thus you must have an existing Windows domain controller (DC) with WMI support in your domain. For example, you can a Windows Server 2008 or 2008 R2 DC as replication partner during the join. For further information, see Joining a Windows Server 2008 / 2008 R2 DC to a Samba AD.
Network Configuration
- Click the "Start" button, search for "View network connections", and open the search entry.
- Right-click to your network adapter and select "Properties".
- Configure the IP settings:
- Assign a static IP address, enter the subnet mask, and default gateway.
- Enter the IP of a DNS server that is able to resolve the Active Directory (AD) DNS zone.
- Click "OK" to save the settings.
Date and Time Settings
Active Directory uses Kerberos for authentication. Kerberos requires that the domain member and the domain controllers (DC) are having a synchronous time. If the difference exceeds 5 minutes (default), the client is not able to access domain resources for security reasons.
Before you join the domain, check the time configuration:
- Open the "Control Panel".
- Navigrate to "Clock, Language and Region".
- Click "Date and Time".
- Verify the date, time, and time zone settings. Adjust the settings, if necessary.
- Click "OK" to save the changes.
FSMO Roles
When you join the first Windows Server 2012 or 2012 R2 host as a domain controller (DC) to an Active Directory (AD) forest, the directory schema and the domain are updated. This update must run on a Windows 2008 or 2008 R2 domain controller (DC). For updating the forest and directory schema, transfer the following two flexible single master operation (FSMO) roles to the Windows DC that is already a domain member:
- Schema Master
- Infrastructure Master
To transfer the two FSMO roles to a Windows Server 2008 or 2008 R2 DC, see Transfering and Seizing FSMO_Roles.
If you successfully updated the schema during the first Windows Server 2012 or 2012 R2 join, you can later transfer the roles to a Samba DC again.
Note that this is a necesary requirement and the forest or domain preparation fails if a Samba DC holds one or both roles during the first Windows Server 2012 or 2012 R2 DC is joined!
Installing the Active Directory Domain Services
- Start the "Server Manager".
- Click "Add roles and features".
- Select "Role-based or feature-based installation" and click "Next".
- Click "Select a server from the server pool" and select the local Windows Server from the list. Click "Next".
- Select "Active Directory Domain Services", including all dependencies. Click "Next".
- You do not need to select any additional features. Click "Next".
- Start the installation.
- Click "Close".
Joining the Windows Server to the Domain
- Log in to your Windows Server 2012 or 2012 installation using the local administrator account.
- Start the "Server Manager".
- Click the notifier icon on the top navigation bar and click "Promote this server to a domain controller".
- Select "Add a domain controller to an existing domain", enter the Samba Active Directory (AD) domain name and credentials that are enabled to join a domain controller (DC) to the domain, like the domain administrator account. Click "Next".
- Select the options to enable on the new DC and enter the directory services restore mode (DSRM) password. It is required to boot the Windows DC in safe-mode to restore or repair the AD in case of problems. Click "Next".
- If you enabled the "DNS server" option in the previous step, you may see a note, that a delegation for this DNS server cannot be created. Click "Next".
- Samba currently does not support schema replication using the Windows management instrumentation (WMI) protocol. For this reason, select an existing Windows Domain Controller in the domain as replication source and click "Next".
- Set the folders for the AD database, log files and the Sysvol folder. Click "Next".
- Click "Next" to confirm the operations, Windows is going to perform.
- Verify your settings and click "Next" to start the prerequisite check.
- Windows runs some prerequisites checks. If any errors are displayed, fix them before you continue. Click "Install".
- The DC promotions begins.
- If this is the first Windows Server 2012 or 2012 R2 DC in your AD forest:
- Warning: This step breaks the AD directory replication! For more details, see Warning.
- The installation wizzard is only able to run the AD forest preparation. The domain preparation step fails. To work around:
- Log in using the domain administrator account to your existing Windows Server 2008 or 2008 R2 installation that owns the "Schema Master" and the "Infrastructure Master" flexible single master operation (FSMO) role.
- Insert the Windows Server 2012 or Windows 2012 R2 installation DVD.
- Open a command line and change to the "support\adprep" folder on the installation DVD. For example, if you DVD drive is "D":
> D: > cd support\adprep\
- Start the domain preparation:
> adprep /domainprep
- You see the following message if the preparation succeeds:
Adprep successfully updated the domain-wide information.
- Restart the Joining the Windows Server to the Domain process.
- If the wizzard completes successfully, the Windows server is restarted automatically.
- Verify that all DC related DNS records have been created during the promotion. See Verifying and Creating a DC DNS Record.
- Do not continue without checking the DNS records. They must exist for a working directory replication!
Verifying the Directory Replication
A few minutes after the domain controller (DC) started, the connections with all other DCs are automatically established and the replication begins.
To verify the directory replication, run on a Samba DC:
# samba-tool drs showrepl
Default-First-Site-Name\SAMBADC
DSA Options: 0x00000001
DSA object GUID: 4a6bd92a-6612-4b15-aa8c-9ec371e8994f
DSA invocationId: 96bc0d6f-9cea-4011-b9a1-0e9971009b20
==== INBOUND NEIGHBORS ====
DC=DomainDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=ForestDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=ForestDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:35:09 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:09 2014 CET
DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:35:09 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:09 2014 CET
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:35:10 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:10 2014 CET
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:35:10 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:10 2014 CET
CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:35:11 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:11 2014 CET
CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:35:11 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:11 2014 CET
==== OUTBOUND NEIGHBORS ====
DC=DomainDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:17 2014 CET
DC=DomainDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:17 2014 CET
DC=ForestDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:17 2014 CET
DC=ForestDnsZones,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:35:17 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:35:17 2014 CET
DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:34:26 2014 CET
DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:34:26 2014 CET
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:34:26 2014 CET
CN=Schema,CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:34:26 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:34:26 2014 CET
CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2008R2DC via RPC
DSA object GUID: dfaec3fb-7546-4153-ba01-605e5efa27f9
Last attempt @ Sat Dec 20 10:34:21 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:34:21 2014 CET
CN=Configuration,DC=samdom,DC=example,DC=com
Default-First-Site-Name\Win2012R2DC via RPC
DSA object GUID: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Last attempt @ Sat Dec 20 10:34:21 2014 CET was successful
0 consecutive failure(s).
Last success @ Sat Dec 20 10:34:21 2014 CET
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: f55bce90-d458-400a-a4ca-801c3e64bef3
Enabled : TRUE
Server DNS name : Win2008R2DC.samdom.example.com
Server DN name : CN=NTDS Settings,CN=Win2008R2DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
Connection --
Connection name: fb03f58b-1654-4a02-8e11-f0ea120b60cc
Enabled : TRUE
Server DNS name : Win2012R2DC.samdom.example.com
Server DN name : CN=NTDS Settings,CN=Win2012R2DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
It can take several minutes until all connections are established. If the connections on existing Samba DCs to the Windows DC are not established within 15 minutes, start the replication manually. For details, see samba-tool drs replicate.
If you are seeing the warning "No NC replicated for Connection!", see FAQ: Warning: No NC replicated for Connection!.
Testing the Directory Replication
To test that the directory replication works correctly, add for example a user on an existing DC and verify that it shows up automatically on the new promoted Windows DC.
During the join, Windows tries to replicate the Sysvol directory content from an existing domain controller (DC). Samba currently does not support the DFS-R protocol. For this reason, the new DC may not show a "Sysvol" share. To enable the share:
- Save the following content to a plain text file named "Win-Create-Sysvol-Share.reg" using a text editor like "Notepad" or "Editor" (not Word/Wordpad/OpenOffice/LibreOffice/etc.):
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters] "SysvolReady"=dword:00000001
- Log in using an account that is member of the local "Administrators" group.
- Double-click the file to import it to the Windows registry.
- Reboot to take the changes effect.
Sysvol replication
Samba currently does not support the DFS-R protocol required for Sysvol replication. Please manually synchronise the content between DC or use a workaround like Robocopy-based Sysvol Replication.