Demoting a Samba AD DC: Difference between revisions
From SambaWiki
m (→Demote a still working Domain Controller: update about the 7 fsmo roles) |
mNo edit summary |
||
| (33 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
= Introduction = |
= Introduction = |
||
Sometimes, you may find it necessary to permanently remove a domain controller (DC) from Active Directory (AD). Removing a regular domain member only requires the deletion of the machine account entry, but, to remove a DC from AD, you have to demote it. |
|||
Whenever a Domain Controller needs to be removed from your domain, for what ever reason, you will have to demote it. This HowTo describes different scenarios to demote a Domain Controller. |
|||
If a DC is not demoted correctly, your AD can get unstable. For example: |
|||
* replication failures can occur. |
|||
* the remaining DCs can slow down due to time outs and failed replication attempts. |
|||
* log ins on domain members can fail or take longer. |
|||
== Server information used in this HowTo == |
|||
= Demoting an Online Domain Controller = |
|||
Inside this HowTo, we will be using the following configuration/settings: |
|||
If the domain controller (DC) to demote is still working correctly: |
|||
Installation directory: /usr/local/samba/ |
|||
DC to demote: DC2 |
|||
Different DC remaining in the network: DC1 |
|||
DNS Domain Name/Realm: samdom.example.com |
|||
NT4 Domain Name: samdom |
|||
* Log in locally to the DC you wish to demote. |
|||
= Demote a still working Domain Controller = |
|||
* Ensure the <code>samba</code> service is running. |
|||
Follow this section, if your DC is accessable and working. |
|||
* Check if the DC owns any flexible single master operations (FSMO) roles. See [[Transferring_and_Seizing_FSMO_Roles#Displaying_the_Current_FSMO_Role_Owners|Displaying the Current FSMO Role Owners]]. |
|||
* Log into the DC you want to demote. |
|||
: If the DC does own any FSMO roles, transfer them to a different DC. See [[Transferring_and_Seizing_FSMO_Roles#Transferring_an_FSMO_Role|Transferring an FSMO Role]]. |
|||
* Verify that the DC is not the last one remaining in the domain! |
|||
* Optionally, display the objectGUID of the DC. For example, for the <code>DC2</code> host: |
|||
* Make sure, that this DC does not contain any [[Flexible_Single-Master_Operations_(FSMO)_roles|FSMO role]]: |
|||
# ldbsearch -H /usr/local/samba/private/sam.ldb '(invocationId=*)' --cross-ncs objectguid | grep -A1 DC2 |
|||
# samba-tool fsmo show |
|||
dn: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
objectGUID: c14a774f-9732-4ec2-b9fa-2156c95c4e48 |
|||
RidAllocationMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
PdcEmulationMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
DomainNamingMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
SchemaMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
: If you want to verify that all DNS entries were deleted after you demoted the DC, you need to know the host name, IP address, and the objectGUID of the DC. |
|||
* If you are using Samba 4.3.0 and up, the samba tool command will show an extra two FSMO roles: |
|||
DomainDnsZonesMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
ForestDnsZonesMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Irrespective of version, there are 7 FSMO roles, see [[Transfering_/_seizing_FSMO_roles#Show_current_FSMO_role_owners|show fsmo roles]] for how to display all 7 roles on earlier versions. |
|||
: If it still contains one or more [[Flexible_Single-Master_Operations_(FSMO)_roles#Transfering_a_FSMO_role|FSMO roles, transfer]] them to a different DC. |
|||
* Demote the DC: |
* Demote the DC: |
||
| Line 48: | Line 37: | ||
Using DC1.samdom.example.com as partner server for the demotion |
Using DC1.samdom.example.com as partner server for the demotion |
||
Password for [SAMDOM\administrator]: |
Password for [SAMDOM\administrator]: |
||
Deactivating inbound replication |
|||
Asking partner server DC1.samdom.example.com to synchronize from us |
Asking partner server DC1.samdom.example.com to synchronize from us |
||
Changing userControl and container |
Changing userControl and container |
||
Removing Sysvol reference: CN=DC2,CN=Enterprise,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Demote successfull |
|||
Removing Sysvol reference: CN=DC2,CN=samdom.example.com,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Removing Sysvol reference: CN=DC2,CN=Domain System Volumes (SYSVOL share),CN=File Replication Service,CN=System,DC=samdom,DC=example,DC=com |
|||
Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com |
|||
Demote successful |
|||
* Stop the <code>samba</code> service. |
|||
* If the DC used the <code>BIND9_DLZ</code> DNS back end for the Active Directory (AD) zones: |
|||
:* stop the Bind9 DNS service. |
|||
:* verify that no members of the domain use this host to resolve the AD DNS zones. |
|||
= Demoting an Offline Domain Controller = |
|||
In certain situations, such as hardware failures, it is necessary to remove a non accessible domain controller (DC) from the domain. In this case, you must demote the DC using a remaining working Samba DC. |
|||
{{Imbox |
|||
| type = important |
|||
| text = Only run this procedure if the DC to demote is no longer connected to the AD and you cannot demote it as described in [[#Demoting_an_Online_Domain_Controller|Demoting an Online Domain Controller]]. This ensures that all changes, like password changes, are replicated onto another DC. Otherwise such changes will be lost. You can get a list of changes by using [[Samba-tool ldapcmp]]. |
|||
}} |
|||
To remotely demote an offline DC: |
|||
* Log in to a working Samba DC in the Active Directory (AD) forest. |
|||
* Verify that Samba 4.4 or later is installed: |
|||
# samba --version |
|||
{{Imbox |
|||
| type = important |
|||
| text = You cannot demote an offline remote DC from a DC that runs Samba 4.4 or earlier. Update to Samba 4.4.0 or later before you continue. For details, see [[Updating Samba]]. |
|||
}} |
|||
* Check that the remote DC being demoted does not own any flexible single master operations (FSMO) role. See [[Transferring_and_Seizing_FSMO_Roles#Displaying_the_Current_FSMO_Role_Owners|Displaying the Current FSMO Role Owners]]. |
|||
:* If the DC being demoted owns any FSMO roles, seize them to the local DC. See [[Transferring_and_Seizing_FSMO_Roles#Transferring_and_Seizing_FSMO_Roles#Seizing_a_FSMO_Role|Seizing an FSMO Role]]. |
|||
* Verify that the DC being demoted is turned off. |
|||
* Optionally, display the objectGUID of the DC. For example, for the <code>DC2</code> host: |
|||
# ldbsearch -H /usr/local/samba/private/sam.ldb '(invocationId=*)' --cross-ncs objectguid | grep -A1 DC2 |
|||
dn: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
objectGUID: c14a774f-9732-4ec2-b9fa-2156c95c4e48 |
|||
: If you want to verify that all DNS entries were deleted after you demoted the DC, you need to know the host name, IP address, and the objectGUID of the DC. |
|||
* Demote the remote DC. For example, to demote <code>DC2</code>: |
|||
# samba-tool domain demote --remove-other-dead-server=DC2 |
|||
Removing nTDSConnection: CN=04baf417-eb41-4f31-a5f1-c739f0e92b1b,CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Removing nTDSDSA: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com (and any children) |
|||
Removing RID Set: CN=RID Set,CN=DC2,OU=Domain Controllers,DC=samdom,DC=example,DC=com |
|||
Removing computer account: CN=DC2,OU=Domain Controllers,DC=samdom,DC=example,DC=com (and any child objects) |
|||
Removing Samba-specific DNS service account: CN=dns-DC2,CN=Users,DC=samdom,DC=example,DC=com |
|||
updating samdom.example.com keeping 3 values, removing 1 values |
|||
updating DC=_kerberos._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_gc._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_kerberos._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_kerberos._udp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_kpasswd._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_kpasswd._udp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_gc._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp.4d5258b9-0cd7-4d78-bdd7-99ebe6b19751.domains,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_kerberos._tcp.Default-First-Site-Name._sites.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp.Default-First-Site-Name._sites.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp.Default-First-Site-Name._sites.gc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=c14a774f-9732-4ec2-b9fa-2156c95c4e48,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 0 values, removing 1 values |
|||
updating DC=_kerberos._tcp.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
updating DC=_ldap._tcp.gc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values |
|||
Removing Sysvol reference: CN=DC2,CN=Enterprise,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Removing Sysvol reference: CN=DC2,CN=samdom.example.com,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Removing Sysvol reference: CN=DC2,CN=Domain System Volumes (SYSVOL share),CN=File Replication Service,CN=System,DC=samdom,DC=example,DC=com |
|||
Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com |
|||
:{{Imbox |
|||
* Shutdown Samba |
|||
| type = warning |
|||
| text = You must never reconnect a remotely demoted DC to the network. Your AD can get inconsistent. |
|||
}} |
|||
* If the demoted DC ran a DNS service for the Active Directory (AD) zones, verify that domain members and DCs no longer use this host to resolve the AD DNS zones. |
|||
* [[#Verifying_that_nothing_was_left|Verify that nothing was left]]. |
|||
= Demote a DC that isn't accessable any more= |
|||
Follow this section, if your DC is not accessable any more, e. g. by hardware failure and it surely will never come back into the network. |
|||
samba-tool currently does not support demote a foreign DC. That's why currently the only way to demote a lost DC is using the Windows tools. '''Sadly demoting e. g. through deleting the DC in ADUC, currently fails. See [https://bugzilla.samba.org/show_bug.cgi?id=10595 Bug report #10595].''' |
|||
'''There are suspicion that samba DC with the metadate of the DC that isn't accessible ''would eat up memory and later trigger oom-killer.''''' |
|||
= Verifying the Demotion = |
|||
This information was correct Until 4.1.12, and the same problem might kill the 2nd and 3rd DC if you have. |
|||
To manually verify that the domain controller (DC) was successfully demoted: |
|||
Some people say that they can remove using the script below, but it was fully '''not tested'''. |
|||
Please use at your own risk. |
|||
[http://gallery.technet.microsoft.com/scriptcenter/d31f091f-2642-4ede-9f97-0e1cc4d577f3#content] |
|||
{{Imbox |
|||
= Verifying that nothing was left = |
|||
| type = important |
|||
| text = The steps described in this section, do not replace the official demote procedures described in the previous sections. The steps in this section are only to verify and to manually remove remaining entries, if the official demote process failed. |
|||
}} |
|||
* Log in to a Windows domain member using an account that is member of the <code>Domain Admins</code> group, such as the AD domain Administrator account. |
|||
The following steps are done on a Windows computer having [[Installing RSAT|RSAT installed]]. |
|||
* Install the Remote Server Administration Tools (RSAT). For details, see [[Installing RSAT]]. |
|||
'''Warning: The following are just cleanup steps, if something was left after a demote! It's not a replacement for the demote process itself!''' |
|||
* Open |
* Open the <code>Active Directory Users and Computers</code> application. |
||
:* Navigate to the <code>Domain Controllers</code> entry and verify that the demoted DC was removed. For example: |
|||
:* Go to the container „Domain Controllers“ and verify that the demoted DC was removed. If not, remove the account manually. This would also cleanup metadata. '''DC removal via ADUC is currently broken. See [https://bugzilla.samba.org/show_bug.cgi?id=10595 Bug report #10595].''' |
|||
:[[Image:ADUC_Domain_Controllers.png]] |
|||
:* If the entry is still listed, you can manually remove it: |
|||
::* Right-click to the DC entry and select <code>Delete</code> |
|||
::* Click <code>Yes</code> to confirm. |
|||
::* Select <code>Delete this Domain Controller anyway. It is permanently offline and can no longer be removed using the removal wizard.</code> and click <code>OK</code>. |
|||
::* If the DC is a global catalog server, click <code>Yes</code> to confirm. |
|||
* Open the <code>Active Directory Sites and Services</code> application and verify that the demoted DC is no longer listed in any Active Directory (AD) site entry. For example: |
|||
: [[Image:ADUC_Domain_Controllers.png]] |
|||
:[[Image:ADSS_Domain_Controllers.png]] |
|||
:* If the entry is still listed, you can manually remove it: |
|||
::* Right-click to the DC entry and select <code>Delete</code> |
|||
::* Click <code>Yes</code> to confirm. |
|||
* Open the <code>DNS</code> application and verify that the DC's host name, IP address, and objectGUID is no longer used in any DNS entry in any AD DNS zone. For example: |
|||
* Open „Active Directory Sites and Services“ |
|||
:[[Image:DNS_Domain_Controllers.png]] |
|||
:* If entries are still listed, you can manually remove them: |
|||
::* Right-click to the entry and select <code>Delete</code> |
|||
::* Click <code>Yes</code> to confirm. |
|||
:* Check that the demoted DC doesn't exist any more in any site. If an entry is still there, remove it manually. |
|||
: [[Image:ADSS_Domain_Controllers.png]] |
|||
* Open the „DNS“ console |
|||
:* <u>Check in all zones</u>, that no entry about the demoted DC is still existing. |
|||
---- |
|||
: [[Image:DNS_Domain_Controllers.png]] |
|||
[[Category:Active Directory]] |
|||
Latest revision as of 15:27, 11 June 2023
Introduction
Sometimes, you may find it necessary to permanently remove a domain controller (DC) from Active Directory (AD). Removing a regular domain member only requires the deletion of the machine account entry, but, to remove a DC from AD, you have to demote it.
If a DC is not demoted correctly, your AD can get unstable. For example:
- replication failures can occur.
- the remaining DCs can slow down due to time outs and failed replication attempts.
- log ins on domain members can fail or take longer.
Demoting an Online Domain Controller
If the domain controller (DC) to demote is still working correctly:
- Log in locally to the DC you wish to demote.
- Ensure the
sambaservice is running.
- Check if the DC owns any flexible single master operations (FSMO) roles. See Displaying the Current FSMO Role Owners.
- If the DC does own any FSMO roles, transfer them to a different DC. See Transferring an FSMO Role.
- Optionally, display the objectGUID of the DC. For example, for the
DC2host:
# ldbsearch -H /usr/local/samba/private/sam.ldb '(invocationId=*)' --cross-ncs objectguid | grep -A1 DC2 dn: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com objectGUID: c14a774f-9732-4ec2-b9fa-2156c95c4e48
- If you want to verify that all DNS entries were deleted after you demoted the DC, you need to know the host name, IP address, and the objectGUID of the DC.
- Demote the DC:
# samba-tool domain demote -Uadministrator Using DC1.samdom.example.com as partner server for the demotion Password for [SAMDOM\administrator]: Deactivating inbound replication Asking partner server DC1.samdom.example.com to synchronize from us Changing userControl and container Removing Sysvol reference: CN=DC2,CN=Enterprise,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=samdom.example.com,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=Domain System Volumes (SYSVOL share),CN=File Replication Service,CN=System,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com Demote successful
- Stop the
sambaservice.
- If the DC used the
BIND9_DLZDNS back end for the Active Directory (AD) zones:
- stop the Bind9 DNS service.
- verify that no members of the domain use this host to resolve the AD DNS zones.
Demoting an Offline Domain Controller
In certain situations, such as hardware failures, it is necessary to remove a non accessible domain controller (DC) from the domain. In this case, you must demote the DC using a remaining working Samba DC.
| Only run this procedure if the DC to demote is no longer connected to the AD and you cannot demote it as described in Demoting an Online Domain Controller. This ensures that all changes, like password changes, are replicated onto another DC. Otherwise such changes will be lost. You can get a list of changes by using Samba-tool ldapcmp. |
To remotely demote an offline DC:
- Log in to a working Samba DC in the Active Directory (AD) forest.
- Verify that Samba 4.4 or later is installed:
# samba --version
| You cannot demote an offline remote DC from a DC that runs Samba 4.4 or earlier. Update to Samba 4.4.0 or later before you continue. For details, see Updating Samba. |
- Check that the remote DC being demoted does not own any flexible single master operations (FSMO) role. See Displaying the Current FSMO Role Owners.
- If the DC being demoted owns any FSMO roles, seize them to the local DC. See Seizing an FSMO Role.
- Verify that the DC being demoted is turned off.
- Optionally, display the objectGUID of the DC. For example, for the
DC2host:
# ldbsearch -H /usr/local/samba/private/sam.ldb '(invocationId=*)' --cross-ncs objectguid | grep -A1 DC2 dn: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com objectGUID: c14a774f-9732-4ec2-b9fa-2156c95c4e48
- If you want to verify that all DNS entries were deleted after you demoted the DC, you need to know the host name, IP address, and the objectGUID of the DC.
- Demote the remote DC. For example, to demote
DC2:
# samba-tool domain demote --remove-other-dead-server=DC2 Removing nTDSConnection: CN=04baf417-eb41-4f31-a5f1-c739f0e92b1b,CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com Removing nTDSDSA: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com (and any children) Removing RID Set: CN=RID Set,CN=DC2,OU=Domain Controllers,DC=samdom,DC=example,DC=com Removing computer account: CN=DC2,OU=Domain Controllers,DC=samdom,DC=example,DC=com (and any child objects) Removing Samba-specific DNS service account: CN=dns-DC2,CN=Users,DC=samdom,DC=example,DC=com updating samdom.example.com keeping 3 values, removing 1 values updating DC=_kerberos._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_gc._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kerberos._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kerberos._udp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kpasswd._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kpasswd._udp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_gc._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.4d5258b9-0cd7-4d78-bdd7-99ebe6b19751.domains,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kerberos._tcp.Default-First-Site-Name._sites.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.Default-First-Site-Name._sites.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.Default-First-Site-Name._sites.gc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=c14a774f-9732-4ec2-b9fa-2156c95c4e48,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 0 values, removing 1 values updating DC=_kerberos._tcp.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.gc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values Removing Sysvol reference: CN=DC2,CN=Enterprise,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=samdom.example.com,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=Domain System Volumes (SYSVOL share),CN=File Replication Service,CN=System,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com

You must never reconnect a remotely demoted DC to the network. Your AD can get inconsistent.
- If the demoted DC ran a DNS service for the Active Directory (AD) zones, verify that domain members and DCs no longer use this host to resolve the AD DNS zones.
Verifying the Demotion
To manually verify that the domain controller (DC) was successfully demoted:
| The steps described in this section, do not replace the official demote procedures described in the previous sections. The steps in this section are only to verify and to manually remove remaining entries, if the official demote process failed. |
- Log in to a Windows domain member using an account that is member of the
Domain Adminsgroup, such as the AD domain Administrator account.
- Install the Remote Server Administration Tools (RSAT). For details, see Installing RSAT.
- Open the
Active Directory Users and Computersapplication.
- Navigate to the
Domain Controllersentry and verify that the demoted DC was removed. For example:
- Navigate to the
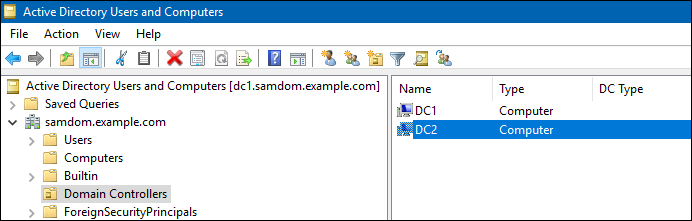
- If the entry is still listed, you can manually remove it:
- Right-click to the DC entry and select
Delete - Click
Yesto confirm. - Select
Delete this Domain Controller anyway. It is permanently offline and can no longer be removed using the removal wizard.and clickOK. - If the DC is a global catalog server, click
Yesto confirm.
- Right-click to the DC entry and select
- Open the
Active Directory Sites and Servicesapplication and verify that the demoted DC is no longer listed in any Active Directory (AD) site entry. For example:
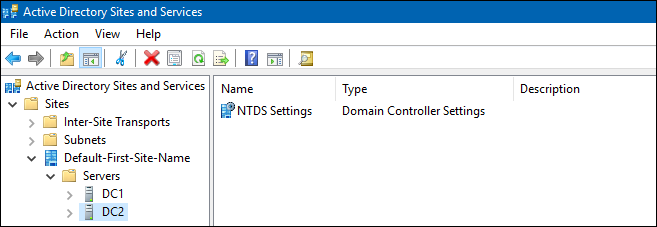
- If the entry is still listed, you can manually remove it:
- Right-click to the DC entry and select
Delete - Click
Yesto confirm.
- Right-click to the DC entry and select
- Open the
DNSapplication and verify that the DC's host name, IP address, and objectGUID is no longer used in any DNS entry in any AD DNS zone. For example:
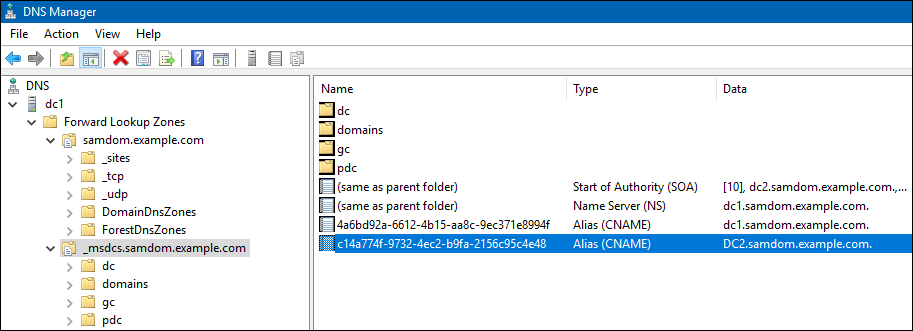
- If entries are still listed, you can manually remove them:
- Right-click to the entry and select
Delete - Click
Yesto confirm.
- Right-click to the entry and select