Demoting a Samba AD DC: Difference between revisions
From SambaWiki
Mmuehlfeld (talk | contribs) m (Fix link) |
Mmuehlfeld (talk | contribs) (Rewrote page) |
||
| Line 1: | Line 1: | ||
= Introduction = |
= Introduction = |
||
If you keep information about a domain controller (DC) that was permanently removed from the Active Directory (AD) in the directory, clients can encounter timeouts during log ins or other operations. To permanently remove a Samba DC from the AD, you must demote it. |
|||
Whenever a Domain Controller needs to be removed from your domain, for what ever reason, you will have to demote it. This documentation describes different scenarios to demote a Domain Controller. |
|||
'''See the [[Host_information_used_in_documentation|host information used in documentation]] page for used paths, hostnames, etc.''' |
|||
| ⚫ | |||
If you domain controller (DC) is still accessible: |
|||
| ⚫ | |||
* Log in to the DC you want to demote. |
|||
* Verify that the DC does not hold any FSMO role. See [[Transfering_and_Seizing_FSMO_Roles#Displaying_the_Current_FSMO_Role_Owners|Displaying the Current FSMO Role Owners]]. |
|||
* Log into the DC you want to demote. |
|||
:* If the DC holds one or more FSMO roles, you must transfer them to a different DC. See [[Transfering_and_Seizing_FSMO_Roles#Transferring_an_FSMO_Role|Transferring an FSMO Role]]. |
|||
* Verify that the DC is not the last one remaining in the domain! |
|||
* Make sure this DC does not contain any [[Flexible_Single-Master_Operations_(FSMO)_roles|FSMO role]]: |
|||
# samba-tool fsmo show |
|||
InfrastructureMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
RidAllocationMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
PdcEmulationMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
DomainNamingMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
SchemaMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
* If you are using Samba 4.3.0 and up, the samba tool command will show an extra two FSMO roles: |
|||
DomainDnsZonesMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
ForestDnsZonesMasterRole owner: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com |
|||
Irrespective of version, there are 7 FSMO roles. See [[Transfering_and_Seizing_FSMO_Roles#Show_Current_FSMO_Role_Owners|show fsmo roles]] for how to display all 7 roles on earlier versions. |
|||
: If it still contains one or more [[Flexible_Single-Master_Operations_(FSMO)_roles#Transfering_a_FSMO_role|FSMO roles, transfer]] them to a different DC. |
|||
* Demote the DC: |
* Demote the DC: |
||
| Line 45: | Line 27: | ||
Demote successfull |
Demote successfull |
||
* Shut down the "samba" service. |
|||
* Shutdown Samba |
|||
* [[#Verifying_that_nothing_was_left|Verify that nothing was left]]. |
|||
= Demote an Offline Domain Controller = |
|||
Only follow this procedure if the domain controller (DC) to demote is no longer accessible; for example, due to a hardware failure: |
|||
= Demote a DC that isn't accessible any more= |
|||
* Log in to a remaining DC. |
|||
| ⚫ | |||
* Verify that you are running Samba 4.4 or a later version: |
|||
Follow this section if your DC is not accessible any more - e. g. by hardware failure - and it surely will never come back into the network. |
|||
# samba --version |
|||
Run the following command on one of the remaining, working Domain Controllers: |
|||
Version 4.5.0 |
|||
| ⚫ | |||
* Verify that the DC to demote does not hold any FSMO role. See [[Transfering_and_Seizing_FSMO_Roles#Displaying_the_Current_FSMO_Role_Owners|Displaying the Current FSMO Role Owners]]. |
|||
:* If the DC holds one or more FSMO roles, you must seize them. See [[Transfering_and_Seizing_FSMO_Roles#Transfering_and_Seizing_FSMO_Roles#Seizing_a_FSMO_Role|Seizing an FSMO Role]]. |
|||
* To demote a remote DC, for example "DC2": |
|||
# samba-tool domain demote --remove-other-dead-server=DC2 |
# samba-tool domain demote --remove-other-dead-server=DC2 |
||
| Line 90: | Line 81: | ||
Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com |
Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com |
||
'''WARNING: Never reconnect a DC to the network, that was demoted using this way. It can cause data loss!''' |
|||
| ⚫ | |||
| ⚫ | |||
The following steps are done on a Windows computer having [[Installing RSAT|RSAT installed]]. |
|||
The following steps are to verify and clean up remaining directory information after a domain controller demotion. It does not replace the procedure for the demote itself! |
|||
* Log on as Domain Administrator to a Windows computer having the Microsoft Remote Server Administration Tools (RSAT) installed. See [[Installing_RSAT|Installing RSAT]. |
|||
* Open „Active Directory Users and Computers“ |
|||
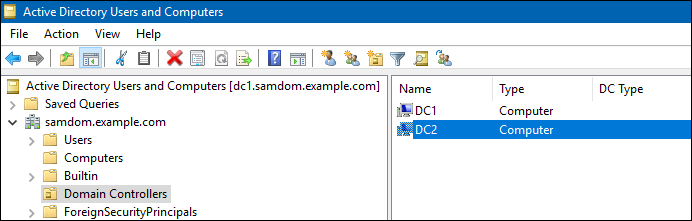
* Start "Active Directory Users and Computers", navigate to the "Domain Controllers" container and verify that the demoted DC was removed. |
|||
:* Go to the container „Domain Controllers“ and verify that the demoted DC was removed. If not, remove the account manually. This would also cleanup metadata. '''DC removal via ADUC is currently broken. See [https://bugzilla.samba.org/show_bug.cgi?id=10595 Bug report #10595].''' |
|||
: [[Image:ADUC_Domain_Controllers.png]] |
: [[Image:ADUC_Domain_Controllers.png]] |
||
* |
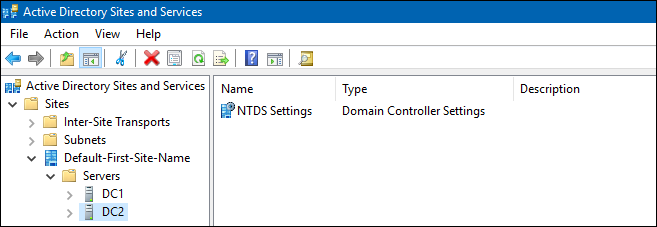
* Start "Active Directory Sites and Services" and check that the demoted DC is not listed in any site. |
||
:* Check that the demoted DC doesn't exist any more in any site. If an entry is still there, remove it manually. |
|||
: [[Image:ADSS_Domain_Controllers.png]] |
: [[Image:ADSS_Domain_Controllers.png]] |
||
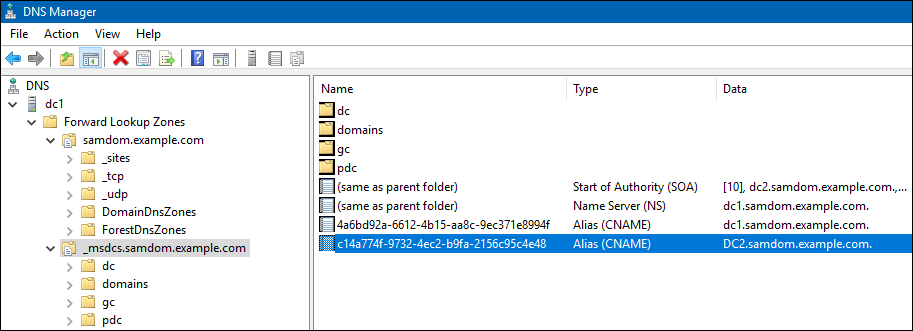
* Start the "DNS" MMC console and check in <u>all</u> zones, that no entry refering to the demoted DC or it's IP has been left. |
|||
* Open the „DNS“ console |
|||
:* <u>Check in all zones</u>, that no entry about the demoted DC is still existing. |
|||
: [[Image:DNS_Domain_Controllers.png]] |
: [[Image:DNS_Domain_Controllers.png]] |
||
Revision as of 13:23, 3 October 2016
Introduction
If you keep information about a domain controller (DC) that was permanently removed from the Active Directory (AD) in the directory, clients can encounter timeouts during log ins or other operations. To permanently remove a Samba DC from the AD, you must demote it.
Demote a Working Domain Controller
If you domain controller (DC) is still accessible:
- Log in to the DC you want to demote.
- Verify that the DC does not hold any FSMO role. See Displaying the Current FSMO Role Owners.
- If the DC holds one or more FSMO roles, you must transfer them to a different DC. See Transferring an FSMO Role.
- Demote the DC:
# samba-tool domain demote -Uadministrator Using DC1.samdom.example.com as partner server for the demotion Password for [SAMDOM\administrator]: Desactivating inbound replication Asking partner server DC1.samdom.example.com to synchronize from us Changing userControl and container Demote successfull
- Shut down the "samba" service.
Demote an Offline Domain Controller
Only follow this procedure if the domain controller (DC) to demote is no longer accessible; for example, due to a hardware failure:
- Log in to a remaining DC.
- Verify that you are running Samba 4.4 or a later version:
# samba --version Version 4.5.0
- Samba version prior 4.4.0 do not support demoting a remote DC. Before you continue, upgrade your existing DCs to 4.4.0 or later.
- Verify that the DC to demote does not hold any FSMO role. See Displaying the Current FSMO Role Owners.
- If the DC holds one or more FSMO roles, you must seize them. See Seizing an FSMO Role.
- To demote a remote DC, for example "DC2":
# samba-tool domain demote --remove-other-dead-server=DC2 Removing nTDSConnection: CN=04baf417-eb41-4f31-a5f1-c739f0e92b1b,CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com Removing nTDSDSA: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=samdom,DC=example,DC=com (and any children) Removing RID Set: CN=RID Set,CN=DC2,OU=Domain Controllers,DC=samdom,DC=example,DC=com Removing computer account: CN=DC2,OU=Domain Controllers,DC=samdom,DC=example,DC=com (and any child objects) Removing Samba-specific DNS service account: CN=dns-DC2,CN=Users,DC=samdom,DC=example,DC=com updating samdom.example.com keeping 3 values, removing 1 values updating DC=_kerberos._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_gc._tcp.Default-First-Site-Name._sites,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kerberos._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kerberos._udp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kpasswd._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kpasswd._udp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_gc._tcp,DC=samdom.example.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.4d5258b9-0cd7-4d78-bdd7-99ebe6b19751.domains,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_kerberos._tcp.Default-First-Site-Name._sites.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.Default-First-Site-Name._sites.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.Default-First-Site-Name._sites.gc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=c14a774f-9732-4ec2-b9fa-2156c95c4e48,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 0 values, removing 1 values updating DC=_kerberos._tcp.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.dc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values updating DC=_ldap._tcp.gc,DC=_msdcs.samdom.example.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=samdom,DC=example,DC=com keeping 1 values, removing 1 values Removing Sysvol reference: CN=DC2,CN=Enterprise,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=samdom.example.com,CN=Microsoft System Volumes,CN=System,CN=Configuration,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=Domain System Volumes (SYSVOL share),CN=File Replication Service,CN=System,DC=samdom,DC=example,DC=com Removing Sysvol reference: CN=DC2,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=samdom,DC=example,DC=com
WARNING: Never reconnect a DC to the network, that was demoted using this way. It can cause data loss!
Verifying the Demotion
The following steps are to verify and clean up remaining directory information after a domain controller demotion. It does not replace the procedure for the demote itself!
- Log on as Domain Administrator to a Windows computer having the Microsoft Remote Server Administration Tools (RSAT) installed. See [[Installing_RSAT|Installing RSAT].
- Start "Active Directory Users and Computers", navigate to the "Domain Controllers" container and verify that the demoted DC was removed.
- Start "Active Directory Sites and Services" and check that the demoted DC is not listed in any site.
- Start the "DNS" MMC console and check in all zones, that no entry refering to the demoted DC or it's IP has been left.