Setting up a Share Using Windows ACLs
Introduction
Extended access control lists (ACL) enable you to set permissions on shares, files, and directories using Windows ACLs and applications. Samba supports shares using extended ACLs on:
- Domain members
- Active Directory (AD) domain controllers (DC)
- NT4 primary domain controller (PDC)
- NT4 backup domain controllers (BDC)
- Standalone hosts
Preparing the Host
You need to set up Samba before you are able to create a share. Depending on what type of Samba server you require, see:
- Setting up Samba as a Domain Member
- Setting up Samba as AD DC
- Setting up Samba as an NT4 PDC (Quick Start)
- Setting up Samba as an NT4 BDC
- Setting up Samba as a Standalone Server
File System Support
The file system, the share will be created on, must support:
- user and system
xattrname spaces. - extended access control lists (ACL).
For further details, see File system support.
Samba Extended ACL Support
To create a share with extended access control list (ACL) support, the smbd service must have been built with ACL support enabled. A Samba host working as an Active Directory (AD) domain controller (DC), is always enabled with extended ACL support.
To verify if Samba has been built with ACL support, enter:
# smbd -b | grep HAVE_LIBACL HAVE_LIBACL
If no output is displayed:
- Samba was built using the
--with-acl-support=noparameter. - The Samba
configurescript was unable to locate the required libraries for ACL support. For details, see Package Dependencies Required to Build Samba.
Enable Extended ACL Support on a Unix domain member
Ideally you have a system that supports NFS4 ACLs. The following example is for systems like Linux, where you don't have those kind of ACLs. To configure shares using extended access control lists (ACL) on a Unix domain member, you must enable the support in the smb.conf file. To enable extended ACL support globally, add the following settings to the [global] section of your smb.conf file:
vfs objects = acl_xattr map acl inherit = yes # the next line is only required on Samba versions less than 4.9.0 store dos attributes = yes
| On a Samba Active Directory (AD) domain controller (DC), extended ACL support is automatically enabled globally. You must not enable the support manually. |
Alternatively, to enable extended ACL support only for a specific share, add the parameters to the share's section.
For further details about the parameters, see the smb.conf(5) man page.
Granting the SeDiskOperatorPrivilege Privilege
By default, the BUILTIN\Administrators is the only holder of the SeDiskOperatorPrivilege privilege.
However, the BUILTIN\Administrators group members are: Administrator, Domain Admins and Enterprise Admins. These will inherit the privileges and permissions that BUILTIN\Administrators holds.
This means that if you use 'Administrator', a member of 'Domain Admins' or 'Enterprise Admins' when logged into Windows, then you do not need to grant the SeDiskOperatorPrivilege at all, it is inherited from BUILTIN\Administrators.
| Only users or groups that are known to Unix can be used. This means that if you use the winbind 'ad' backend on Unix domain members, you must add a uidNumber attribute to users, or a gidNumber to groups in AD. |
If you use the winbind 'ad' backend on Unix domain members and you add a gidNumber attribute to the Domain Admins group in AD, you will break the mapping in idmap.ldb. Domain Admins is mapped as ID_TYPE_BOTH in idmap.ldb, this is to allow the group to own files in Sysvol on a Samba AD DC. It is suggested you create a new AD group (Unix Admins for instance), give this group a gidNumber attribute and add it to the Administrators group and then, on Unix, use the group wherever you would normally use Domain Admins. |
If you are using the 'ad' winbind idmap backend, then you should use the 'Unix Admins' group you were advised to create above. However, if you use any other winbind idmap backend (autorid or rid, for instance), then you can use the 'Domain Admins' group.
| It is recommended to grant the privilege to a group instead of individual accounts. This enables you to add and revoke the privilege by updating the group membership. |
To list all users and groups having the SeDiskOperatorPrivilege privilege granted, enter:
# net rpc rights list privileges SeDiskOperatorPrivilege -U "SAMDOM\administrator" Enter administrator's password: SeDiskOperatorPrivilege: BUILTIN\Administrators
If you need to grant the SeDiskOperatorPrivilege privilege, it must be done on the Samba server that holds the share. |
To share the /srv/samba/Demo/ directory using the Demo share name:
- As the
rootuser, create the directory:
# mkdir -p /srv/samba/Demo/
- To enable accounts other than the domain user
Administratorto set permissions on Windows, grantFull control(rwx) to the user or group you granted theSeDiskOperatorPrivilegeprivilege. For example (if using the 'ad' backend):
# chown root:"Unix Admins" /srv/samba/Demo/ # chmod 0770 /srv/samba/Demo/
- Otherwise for any other backend:
# chown root:"Domain Admins" /srv/samba/Demo/ # chmod 0770 /srv/samba/Demo/
- Add the
[Demo]share definition to yoursmb.conffile:
[Demo]
path = /srv/samba/Demo/
read only = no
- Further share-specific settings and file system permissions are set using the Windows utilities.

If you set the shares permissions from Windows (The recommended way), you can add the line 'acl_xattr:ignore system acls = yes'to your share. If the line is added, Samba will ignore the standard Unix system ACL's (ugo). Once the line is added, runningsetfaclon the shares directory will not show any permission modifications you may have made from Windows. You must not add this line until you have set up the share permissions from Windows, otherwise you may find that you are denied permission to change the permissions from Windows.. Only add the line if you will only connect to share via Samba.

Do not set ANYadditional share parameters. Adding any additional parameters to the share definition can prevent you from configuring or using the share.
- Reload the Samba configuration:
# smbcontrol all reload-config
When you configure a share with extended access control lists (ACL) support, you set the share permissions using Windows utilities instead of adding parameters to the share section in the smb.conf file.
To set permissions and ACLs on the Demo share:
- Log on to a Windows host using the
SAMDOM\Administratoraccount or an account that is a member of the group that is set as the shares group e.g.SAMDOM\johnwherejohnis a member ofDomain Admins.
- Click
Start, enterComputer Management, and start the application.
- Select
Action/Connect to another computer.
- Enter the name of the Samba host and click
OKto connect the console to the host.
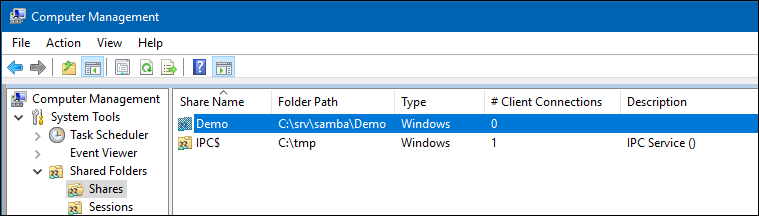
- Open the
System Tools/Shared Folders/Sharesmenu entry.
- Right-click to the share and select
Properties.
| Checking and/or changing the permissions on the 'Share Permissions' tab should not be required, only carry this out if you are having problems, better still, consult the samba mailing list before attempting to use the 'Share Permissions' tab. |
Only users and groups that have been granted the SeDiskOperatorPrivilege privilege can configure the Share Permissions tab. |
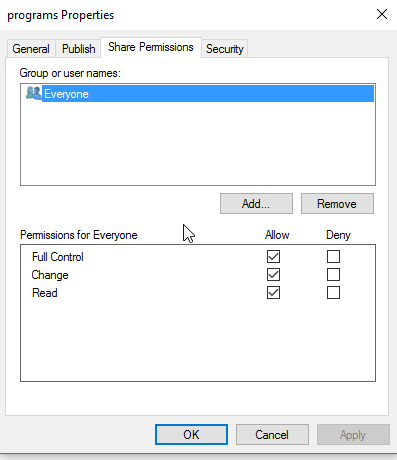
- Select the
Share Permissionstab and check the share permissions, you need to see justEveryone. For example:
If the permissions are as above, do not change anything, if not, change it to just allow Everyone : Full Control, Change and Read. You only make changes to the Security tab. |
- Samba stores the share tab permissions in the
/usr/local/samba/var/locks/share_info.tdbdatabase.
- Select the
Securitytab to make any required permission changes.
| Only the user or members of the group that are set as owner:group set on the servers share directory can configure the Security tab. |
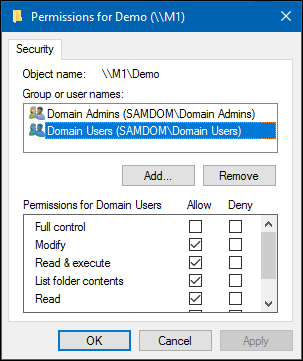
- Click the
Editbutton and set the file system ACLs on the share's root directory. For example:
- For details about using the
SYSTEMaccount on a Samba share see The SYSTEM Account.
- For details where the ACLs are stored, see File System ACLs in the Back End.
- Click the
Addbutton.
- Click
Advancedbutton
- Click
Find Now
- Select a user or group from the list,
Domain Usersfor instance.
- Click
OK
- Click
OK
- Select permissions to grant,
Full controlfor instance.
- A windows security box should open, asking if you want to continue, Click
Yes
- If you check the list of
Group or user names, you should findDomain Userslisted
- Click
OKto close thePermissions for Demowindow.
- Click
OKto store the updated settings.
For further details about configuring share permissions and ACLs, see the Windows documentation.
Setting ACLs on a Folder
To set file system permissions on a folder located on a share that uses extended access control lists (ACL):
- Log on to a Windows host using an account that has
Full controlon the folder you want to modify the file system ACLs.
- Navigate to the folder.
- Right-click to the folder and select
Properties.
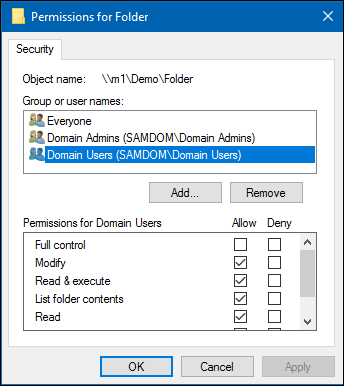
- Select the
Securitytab and click theEditbutton.
- Set the permission. For example:
- For details about using the
SYSTEMaccount on a Samba share see The SYSTEM Account.
- For details where the ACLs are stored, see File System ACLs in the Back End.
- Click
OKto close thePermissions for Folderwindow.
- Click
OKto store the updated settings.
For further details about setting ACLs, see the Windows documentation.
File System ACLs in the Back End
Samba stores the file system permissions in extended file system access control lists (ACL) and in an extended attribute. For example:
- To list the extended ACLs of the
/srv/samba/Demo/directory, enter:
# getfacl /srv/samba/Demo/ # file: srv/samba/Demo/ # owner: root # group: root user::rwx user:root:rwx group::--- group:root:--- group:domain\040users:rwx group:unix\040admins:rwx mask::rwx other::--- default:user::rwx default:user:root:rwx default:group::--- default:group:root:--- default:group:domain\040users:rwx default:group:unix\040admins:rwx default:mask::rwx default:other::---
- To list the
security.NTACLextended attribute of the/srv/samba/Demo/directory, enter:
# getfattr -n security.NTACL -d /srv/samba/Demo/ # file: srv/samba/Demo/ security.NTACL=0sBAAEAAAAAgAEAAIAAQC4zK0lHchKFvwXwbPR/h8P8sXMj5dNIT5QQuWsYwO3RAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAcG9zaXhfYWNsAEbGxuGu39MBuiZRk2pYxeL5ZWc4au0ikqRAk53MkjVd2b4quyk2WwcAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEABJy0AAAA0AAAAAAAAADsAAAAAQUAAAAAAAUVAAAASSVmaZneO8cxOHk/9AEAAAEFAAAAAAAFFQAAAEklZmmZ3jvHMTh5P0oIAAACAMQABwAAAAALFACpABIAAQEAAAAAAAEAAAAAAAAUAAAAEAABAQAAAAAAAQAAAAAACxQA/wEfAAEBAAAAAAADAAAAAAALFACpABIAAQEAAAAAAAMBAAAAAAMkAP8BHwABBQAAAAAABRUAAABJJWZpmd47xzE4eT9KCAAAAAAkAP8BHwABBQAAAAAABRUAAABJJWZpmd47xzE4eT/0AQAAAAMkAL8BEwABBQAAAAAABRUAAABJJWZpmd47xzE4eT8BAgAA
The previous example of file system ACLs and the extended attribute is mapped to the following Windows ACLs:
| Principal | Permissions | Applies to |
|---|---|---|
| Domain Users (SAMDOM\Domain Users) | Modify, Read & execute, List folder contents, Read, Write | (This folder, subfolders and files) |
| Unix Admins (SAMDOM\Unix Admins) | Full control | (This folder, subfolders and files) |
- To get the ACL in a more readable form, enter:
# samba-tool ntacl get /usr/local/samba/var/locks/sysvol --as-sddl # O:BAG:SYD:PAI(A;OICIIO;WOWDGRGWGX;;;CO)(A;OICIIO;GRGX;;;AU)(A;;0x001200a9;;;AU)(A;OICIIO;GA;;;SY)(A;;0x001f01ff;;;SY)(A;OICIIO;WOWDGRGWGX;;;BA)(A;;0x001e01bf;;;BA)(A;OICIIO;GRGX;;;SO)(A;;0x001200a9;;;SO)
Troubleshooting
For troubleshooting, see: